Can You Trust This Page?
Look at the address bar at the top of this page. This page is on blog.bham.ac.uk. This tells you that it is part of the official bham.ac.uk domain owned by the University of Birmingham.
If you came here to verify whether a suspicious email was part of a phishing simulation, then check that the image below matches the email you received.
What we did
On Tuesday 10 February, IT Security sent a simulated phishing email to selected staff. It appeared to be:
- From: YourViewMatters@localuniversitynews.com
- Subject: Vincent Drive and Pritchatt’s Road LTN questionnaire
The email pretended to be a questionnaire from a new campus newspaper. Clicking the link led to a login screen resembling the usual University sign-in page which asked for your University email address and your University password.
Important: No credentials were collected or stored. Anyone who entered details was redirected to a page confirming this was a safe simulation.
An image of the email – with the suspicious parts marked in red and orange
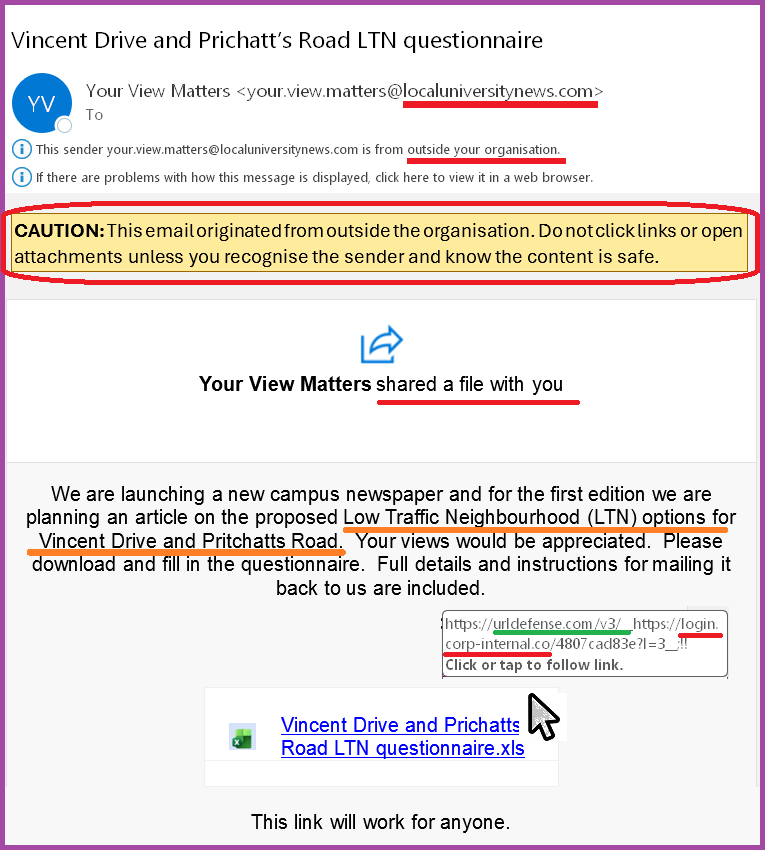
What Made the Email Suspicious?
- It comes from outside the University,
BUT- If the sender is unfamiliar to you and you are not expecting it, you should not trust it.
- A new unknown organisation will not have your email address by legitimate means.
- It is not normal to make initial contact though a file share.
- It looks like a SharePoint file share but the link is to login.corp-internal.co
- The orange-underlined text is about the controversial issue of Low Traffic Neighbourhoods which involves closing roads to cars. Controversial subjects can often move you to act before you think too much.
- Closing roads to two major hospitals, a railway station and University might feel “radical” or “extreme”. But whatever you may think about such a scheme – this email is designed to make you act quickly, without thinking about its genuineness.
- This email does not have many of the tell-tale signs of spam/phishing we may have relied on in the past. This is because attacks are become more sophisticated:
- AI tools can produce grammatically perfect and correctly spelled text.
- Genuine logos and backgrounds are easily copied from the real sites.
- This message aims to create an immediate emotional response (shock, outrage, hope, curiosity) on a controversial topic. A common tactic used by scammers, so that you won’t Pause and Think before you Click.
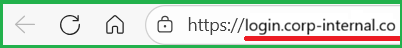
- If you reached the sign-in screen, it looks like your University login but the URL at the top says login.corp-internal.co – which is nothing to do with the University.
NB: scammers often copy real logos and backgrounds from genuine websites to fool you – so always look carefully at the address bar at the top of any sign-in screen.
- It asks for a username and password. Any email which links to a place where you are asked to give your username and password, should be treated with caution.
Pause and Think Before You Click.
- Nothing is so urgent you can’t stop and think, especially if the email makes you feel anxious, angry or moved – you are being rushed into acting.
- Be cautious if an email asks for your username and password. Avoid using a direct email link to reset your password, go the webpage using a browser and login that way.
- Always check the URL of sign-in pages.
- Hover over links (or long-press on mobile) to reveal the full destination address.
About URLDefense
Links in emails may begin with urldefense.com/v3/ — part of our security system that checks external websites for threats.
Even with this protection, you should still inspect the final destination URL to ensure it’s legitimate.
What You Can Do
- Ask yourself:
- Was I expecting this email?
- Do I know the sender?
- Does it “seem right”?
- Is the sign-in screen URL correct?
- Has the email manipulated feelings like urgency, fear, anger, hope, greed?
If you receive a suspicious email:
- Use the Report button in Outlook – it’s faster and helps protect others.
- The Report button trains the system automatically which can automatically quarantine all copies of a problem email.
- If a link seems suspicious then don’t click on it! – even “carefully” to enter dummy details, out of curiosity or “just to be sure”. In a real attack, there is a risk of a “zero-day” “drive by download” which your browser might not protect you against. You are playing with fire.
Why we did this
This exercise is about awareness, not blame
- No one is in any trouble because of this.
- No one will be named or shamed.
- Line managers are not told of any individual’s actions or inactions.
Phishing emails are the top method criminals use to steal passwords, break into systems, steal identities and commit fraud. This simulation is based on real-life threats intercepted by our security systems. These real-world threats often use attention-grabbing “hooks” that tie into current news, trending topics, seasonal events, prizes or workplace-related items such as HR, payroll or IT notices.
Think of it as a fire drill for your Inbox – unexpected, harmless and designed to prepare you for the real thing. This supplements theoretical training. We don’t wait for a real fire to practice escaping – so why wait for a real scam to practice spotting one? Most people accept that a little inconvenience and brief alarm are a small price to pay for stronger security in today’s risky cyber world.
Further quick learning (5-10 mins)
Fraudsters are very devious in using addresses which look similar to genuine ones. This page, from CalTech, shows you how to read URLs (web addresses) correctly, to help you to avoid some of the dirty tricks used https://www.imss.caltech.edu/services/security/recommendations/how-to-read-urls
You can test your knowledge by identifying which of 10 emails are legitimate or phishing in this quiz https://www.phishingbox.com/phishing-iq-test/quiz.php
Questions or Comments?
If you work or study at the University of Birmingham and have questions or comments about this phishing campaign, then contact: itsecurity@contacts.bham.ac.uk
