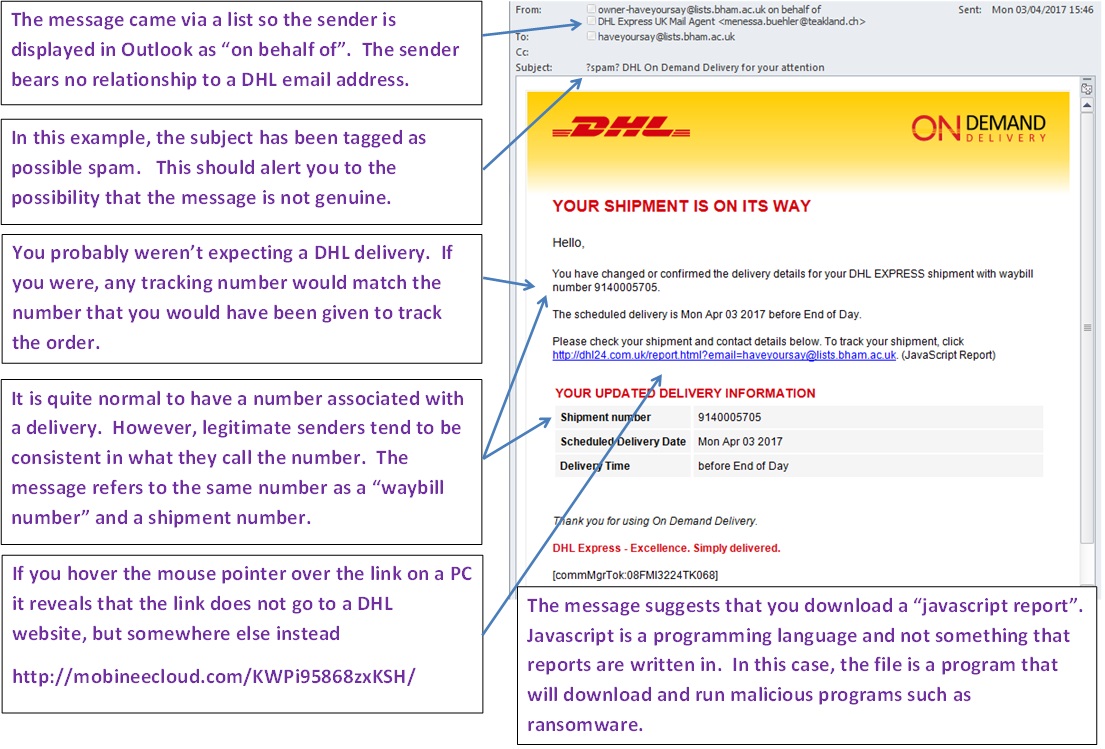
We have received numerous messages containing email claiming to be from DHL about a parcel.
The messages ask you to download a “javascript report”. Javascript is a language for writing programs and not the type of file that would contain a report. This is in fact a javascript program that when run downloads other malicious programs such as ransomware.
This attack was mostly targeted at lists which were open for anyone to post to, which is why many people received multiple copies. Not all list owners use list security features and they allow lists to be posted to from anywhere, which is unnecessary for many lists.
The sender address is unrelated to the company claiming to send it. This in itself is enough to indicate that it is bogus. However, the main giveaway is that parcel companies do not send reports of deliveries in this way; tracking numbers are issued which can be used to track deliveries at company websites.
DHL also offer advice in this area
http://www.dhl.co.uk/en/legal/fraud_awareness.html#spam_viruses

I’ve had several of these arrive – and they’re coming from UNIVERSITY MAILING LISTS
Don’t you think it would be a good idea to tell people about this rather less subtly than the IT services website – a place where only people who suspect the scam might look?
Like – email everyone, right now.
And change the settings on all university mailing lists so that only university addresses on the list (or even only the list owner) can post.
We do not normally email specific warnings about every scam that we are alerted to. This would generate several messages per week and more than one on some days, which would be excessive. Specific warnings can be counter-productive, as some will then see a lack of warning as confirmation that a new scam email is genuine. We do periodically send general warnings about scams; the last one was sent in mid-January. This did publicise the article about how to spot malicious emails (https://blog.bham.ac.uk/itsecurity/2016/12/22/malicious-emails-and-how-to-spot-them/).
However, given the relentless and widespread campaign we did send a message to all members of the University in this case. This was in addition to publicity on the IT services status page and IT Service Desk Twitter feed.
List settings are the responsibility of list owners and there are a variety of controls that can be applied to restrict who can post to the list or request that the list accepts posting from on-campus only. No single set of settings is universally appropriate as lists differ in their requirements. Some lists need to be open for all to post to.
Changing the settings on SOME University mailing lists so that only University addresses on the list (or even only the list owner) can post – could make some lists more or less useless for their intended purpose. The idea has the potential to be suitable for some mail lists but it definitely is not appropriate for ALL lists. So far neither of the two emails I’ve had about DHL deliveries were from any list (University or otherwise).
This is a bit speculative but do you think that really credible scam emails like this are actually *less* successful from the perspective of the perpetrator than more obvious ones? Just thinking that this particular email caught out many people (in my department anyway) who you wouldn’t have thought would fall for them in general. As such it sparks the institution’s “immune system” response and the majority of infected PCs are then quarantined.
Other more obvious scam emails are more likely to be ignored and I’ve read that they often include spelling/grammar mistakes on purpose to self-select their respondents as people who are either more likely to be fooled and less likely to report it. Just wondering how much social engineering factors like this feed into your work really!
The research we have been involved in suggests that the more credible ones have a bigger success rate. The most credible one tested had around a 30% respose rate and the least credible 10%. These were higher responses that we are aware of for the DHL one so far, where the response rates appear to be much lower.
In some cases I believe it is just bad spelling and grammar, just as in some cases payloads fail to deploy because of botched technical implementation. This comment is particularly interesting in the light of a phishing campaign a few weeks ago where there were two versions, with only one version badly worded with mistakes and the other reasonable well worded. It is always difficult to understand the reasoning behind a particular email, when perportrators do not necessarily follow the same thought processes that we would.