Can you trust this page?
If you look in the address bar (at the top of this page) you will see that this page is on the blog.bham.ac.uk site. This tells you that the page is within the bham.ac.uk internet domain which is owned by the University of Birmingham. If you came to this page to confirm if a test phishing email really was a test, then also check that the image of the email below matches the email you were sent. After you have finished on this page, don’t forget to do the brief training offered by our subcontractor Khipu (you will not be asked for your password again!).
On Tuesday 12th March, IT Security sent a number of staff a simulated phishing email claiming Birmingham City Council shared a file with you. The Subject was ‘Proposed Edgbaston Park Rd pedestrianisation’ available through SharePoint, and contained a link to a .docx Word document called Proposed Edgbaston Park Rd pedestrianisation. If you tried to open that document you were asked for your username and password.
Those people who entered a username and password were taken to a page reassuring them this was a benign phishing simulation by IT Security. No passwords were collected or stored!
Why we did this
Our aim is not to penalise, embarrass or make anyone feel bad if they “fell for the scam”. You are not in any trouble. No-one will be “named and shamed”. Your line manager will not be told. We think of this as being like an unannounced fire drill to make people more aware of the most common way that criminals steal passwords.
Criminals usually have more experience in conning honest people, than honest people have in protecting themselves. We want to help you to protect yourself (and the University) by raising awareness of how easy it is to be lured into giving away your personal details and password by malicious emails that appear genuine.
The email – with the suspicious parts marked in red
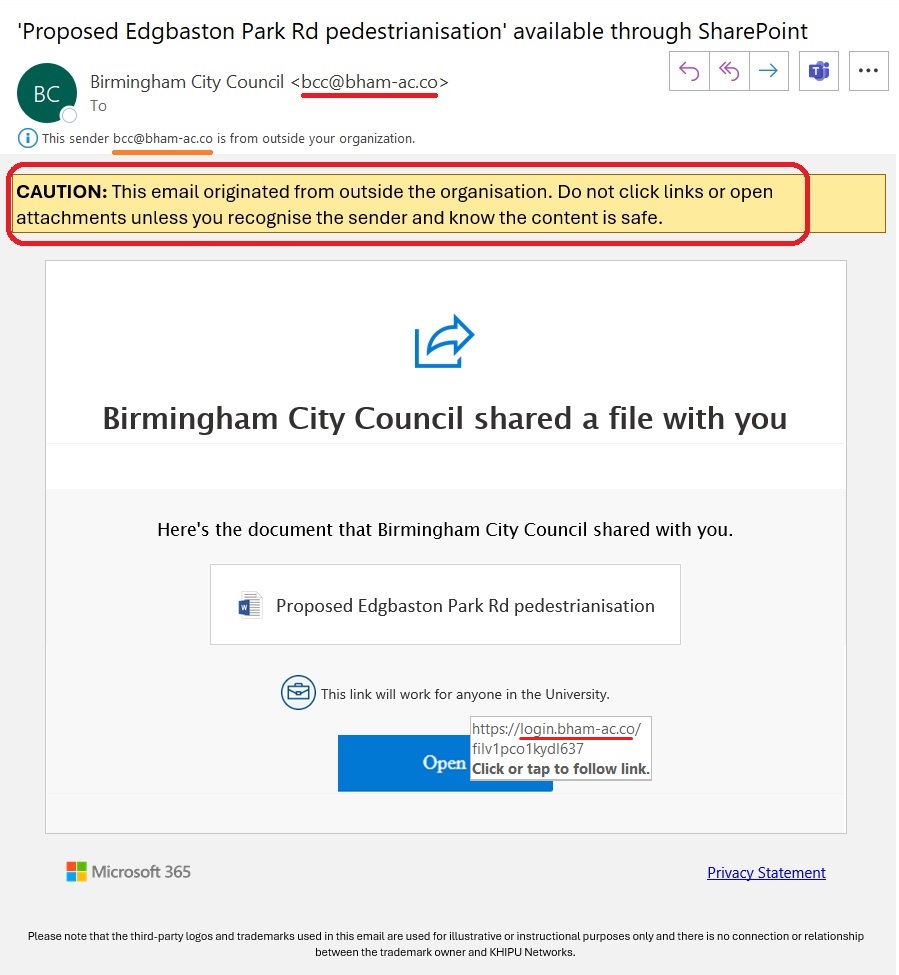
This email is suspicious because:
- If an organization was making an announcement, they would send a message with the announcement in it. They would not share a file without explanation.
- Why would Birmingham City Council contact me via my work email?
Yes – Birmingham City Council might know where I live (if I live in Birmingham).
Yes – I might have given Birmingham City Council my (personal) email address if eg I used that email for Council Tax or Electoral Registration purposes.
BUT – did I give Birmingham City Council my work email? Why would they use my work email address if they already had my personal email eg for Council Tax purposes? - It asks for a username and password. Any email which links to a place where you are asked to give your username and password, should be treated with caution – you should pause, think and ask yourself:
Who is it really from?
Does the sending address match the alleged Sender?
In this case, the Sender’s email domain address is
@bham-ac.co
not
@birmingham.gov.uk
as you would expect from a UK local government authority
Note:
.co at the end of a domain, indicates that it is from the country of Columbia. This domain is popular with scammers who hope that you misread this as .co.uk which indicates UK company.
bham-ac is not the same address as bham.ac.uk . bham.ac.uk is the genuine address, bham-ac.co is an attempt to deceive you.
genuine emails from SharePoint appear to come from no-reply@sharepointonline.com. Fake SharePoint links are regularly used by criminals.
Where does the link take you?
You can reveal the full address:
- on a computer, by hovering the mouse pointer over the link (without clicking on it!)
- on a phone/tablet by a long press holding down on the link.
Microsoft uses various websites and it is sometimes difficult to tell if the link takes you to a genuine Microsoft website or not.
In this example, the Open button links to login.bham-sharepoint.online not hmrc.gov.uk or gov.uk
as you might expect if this was an HMRC or other UK Government communication.
Note: at the University, SharePoint has an address that starts https://bham.my-sharepoint.com.
You should always ask yourself the following:
- was I expecting this email?
- is the Sender known to me?
- and was I expecting them to send/share this file?
Fraudsters are very devious in using addresses which look similar to genuine ones. This page, from CalTech, shows you how to read URLs (web addresses) correctly to help you to avoid some of the dirty tricks used https://www.imss.caltech.edu/services/security/recommendations/how-to-read-urls
You can test your knowledge by identifying which of 10 emails are legitimate or phishing here https://www.phishingbox.com/phishing-iq-test/quiz.php
If you came to this page to confirm that a test phishing email really was a test, then don’t forget to do the short training offered by our subcontractor Khipu.
If you work or study at the University of Birmingham and have questions or comments about this phishing campaign then contact: itsecurity@contacts.bham.ac.uk
